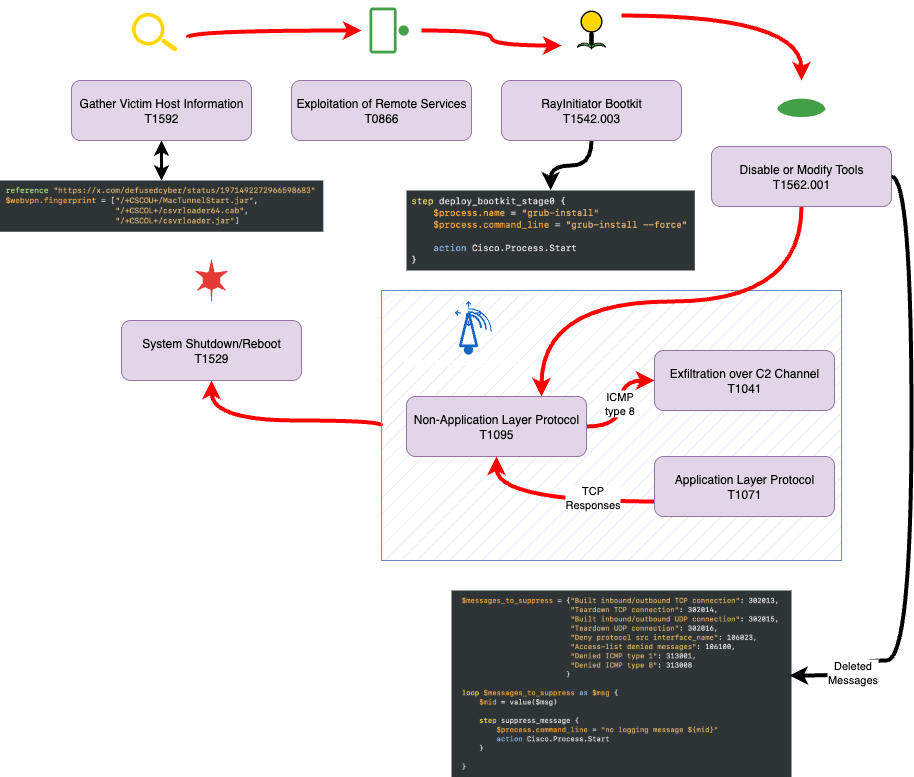
Build Quickly. Test Rapidly. Validate and Deploy in Minutes
Automate detection workflows, Generate any adversary behavior,
Improve detection performance, by automating the detection lifecycle. Anticipate and Adapt your ecosystem to the agility of your adversaries.
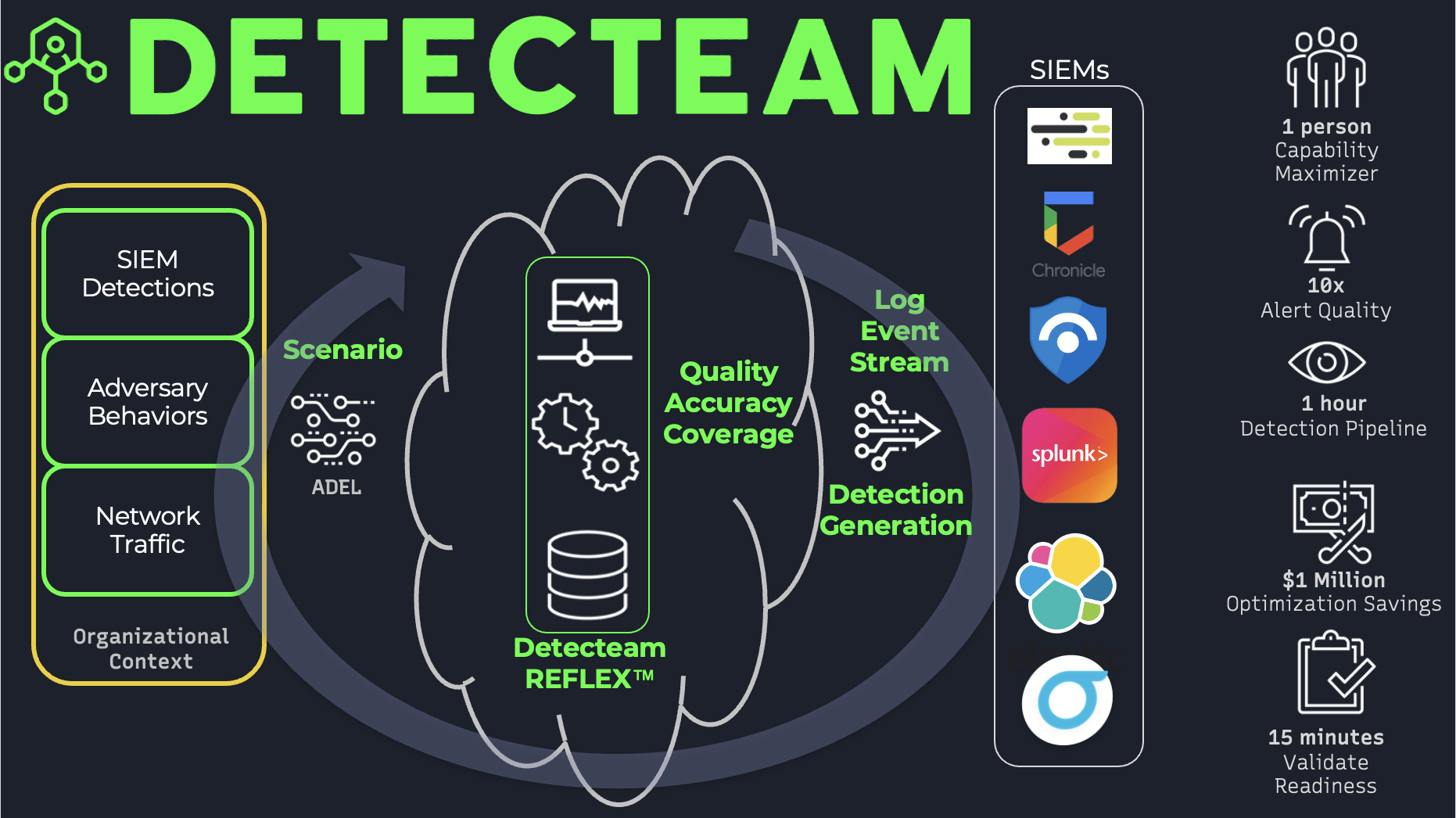
Seamless Integration with Your Favorite Tools





Features & Benefits
THE GOLD STANDARD FOR DETECTION QUALITY AND ADVERSARY READINESS
How fast do you go from a new threat to a detection? Detecteam goes fast, but also includes the required test to validate detection quality.

Massive Attack & Detection Library
Detecteam’s extensive scenario library includes adversary TTPs, detection baselines and simple building blocks like ‘auth failure’ ‘lateral movement’ or detections for ‘all the Mimikatz behaviors’. Use our content library or create your own to evaluate anything from your detection performance to ransomware or powershell execution techniques and much more.

Accurate Adversary Behavior, Precise Data Generation
Generate attack behavior data natively like your SIEM/XDR/Data Lake sees them. Generate accurate detections using the Detecteam REFLEX™ platform’s AI-native automated detection engineering pipeline.

Measure Detection Performance
Baseline what your detections are seeing and what they do not see. Understand detection behavior and performance through metrics and evidence as part of a maturity lifecycle for your SIEM/XDR. Stop thinking in alerts; start thinking in coverage, quality and accuracy.

Detection Lifecycle Automation
Automate detection development workflows across all platforms by building detections faster with fewer resources. Get tested detections into production in minutes not weeks.

AI-Powered Insights
Answer before you are asked if you are prepared for the latest threats. Use our AI-powered Adversary Behavior Builder to Validate your detections behave as you expect when it matters. Improve your detections over time with AI-powered automated improvement and continuous validation you are at peak readiness.
Resource Cost Optimization
Automating detection workflow and detection-as-code development lifecycle dramatically speeds up detection agility. Optimizing technology and security expertise faster, removing tedious manual detection review, reducing time to build, test and deploy and optimizing the cost of detection lifecycle management.
Featured Sections
Why Detecteam?
Detecteam automates operationalizing adversary behaviors and attack trees, generates data representing the behavior, and deploys detections to find this behavior in minutes, not months. Maximize existing staffing and expertise, automate manual building and testing, optimize your security spend and improve your readiness.

Analytics & Reporting
make detections as easy as breathing
With our AI-powered automated workflows, create a scenario, generate data and detections, benchmark your current readiness, or validate emerging threat preparedness in minutes.
Growth & Scaling
Unmatched Flexibility and Scalability
Detecteam leverage your contexts from your different platforms, environments and users. Get your AI custom and tested detections in minutes.


AI Automation
Transform Your Workflow with AI Automation
AI automation manage risk and increase your speed.
Testimonials & Reviews
Hear From Our Happy Clients: Their Stories
Our platform helps customers worldwide for their numerous use-cases on detection and data engineering. Hear from them.

Emily R.
Marketing Lead

We switched from a legacy tool, and I can’t believe the difference. Setup was a breeze, and every question I had was answered within minutes. That level of care is rare.

Mark T
Startup Founder

I love how everything just works. No steep learning curve, no messy configurations—just a clean, powerful product that delivers what it promises.

John Doe
Founder

Beyond the robust features, what really impressed me was the onboarding support. They walked me through everything step-by-step and made us feel valued.

Jason M
Product Manager

The features are great, but the support team truly sets this SaaS apart. From onboarding to daily use, their quick responses and helpful guidance made the whole experience smooth and stress-free. It feels like we have a real partner, not just a service.

Lena K
UX Consultant

This SaaS solution is a gem. It adapts perfectly to our needs, scales effortlessly, and the team behind it feels more like a partner than a provider.

Aliana Lorel
Founder – Lorel Technology

As someone who’s tried countless tools, this one stands out. Performance is solid, updates are regular, and customer service? Simply outstanding.

Sara D
Freelancer

This platform completely transformed how we manage our workflow. The intuitive UI, along with a support team that truly cares, makes it one of the best SaaS experiences I’ve had.

David V
IT Director

Smooth, fast, and reliable. Our team instantly became more productive. The personalized help during onboarding made a huge difference.

Peter Brandson
Owner – Brandson Industry

User-friendly, beautifully designed, and packed with functionality. I’ve never experienced such responsive support. Worth every penny.
Latest News & Articles
Get the latest from the Detecteam blog for the latest threat analysis and scenarios, detection content and more.
Try It Free. Scale When You’re Ready.
Want to turn weeks of trial, error and manual effort into minutes of automation and execution? Get started in minutes.