TLP
TLP CLEAR
Author
Jordi Lobo
Summary
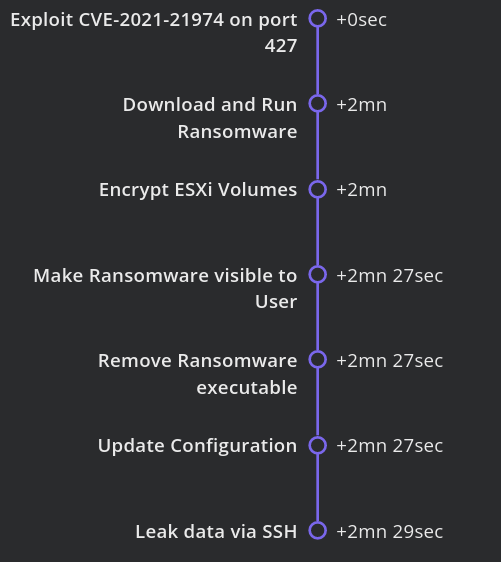
ESXiArgs VMware Ransomware: Massive VMware: Ransomware attack targeting the VMware ESXi hypervisor. Exploits CVE-2021-21974 vulnerability: This vulnerability affects the Service Location Protocol (SLP) service and allows attackers to exploit arbitrary code remotely. The systems currently targeted are ESXi hypervisors in version 6.x, prior to 6.7, CERT-FR stated.
OpenSLP as used in ESXi (7.0 before ESXi70U1c-17325551, 6.7 before ESXi670-202102401-SG, 6.5 before ESXi650-202102101-SG) has a heap-overflow vulnerability. A malicious actor residing within the same network segment as ESXi who has access to port 427 may be able to trigger the heap-overflow issue in OpenSLP service resulting in remote code execution.
The /store/packages/vmtools.py file is the same custom Python backdoor for VMware ESXi server discovered by Juniper in December 2022, allowing the threat actors to remotely access the device.
DATA
TIMELINE
CATEGORY
Ransomware
references
- https://www.bleepingcomputer.com/news/security/massive-esxiargs-ransomware-attack-targets-vmware-esxi-servers-worldwide/
- https://www.csoonline.com/article/3687095/massive-ransomware-attack-targets-vmware-esxi-servers-worldwide.html
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-21974
- https://www.vmware.com/security/advisories/VMSA-2021-0002.html
- https://kb.vmware.com/s/article/76372