TLP
TLP CLEAR
Author
David Deflache
Summary
In May 2023, Barracuda disclosed a zero-day vulnerability (CVE-2023-2868) exploited by UNC4841, a suspected Chinese espionage actor. UNC4841 targeted Barracuda Email Security Gateways (ESG) since October 2022, using malicious email attachments. They deployed code families (SALTWATER, SEASPY, SEASIDE) to infiltrate and maintain control, often disguising as legitimate ESG modules. UNC4841 aggressively sought specific data and conducted lateral movement within victim networks. Barracuda initiated containment and remediation efforts in May 2023, prompting UNC4841 to adapt. The campaign impacted public and private sectors globally, with government agencies among the victims. Mandiant advises isolation and replacement of compromised appliances and further network investigation.
TIMELINE
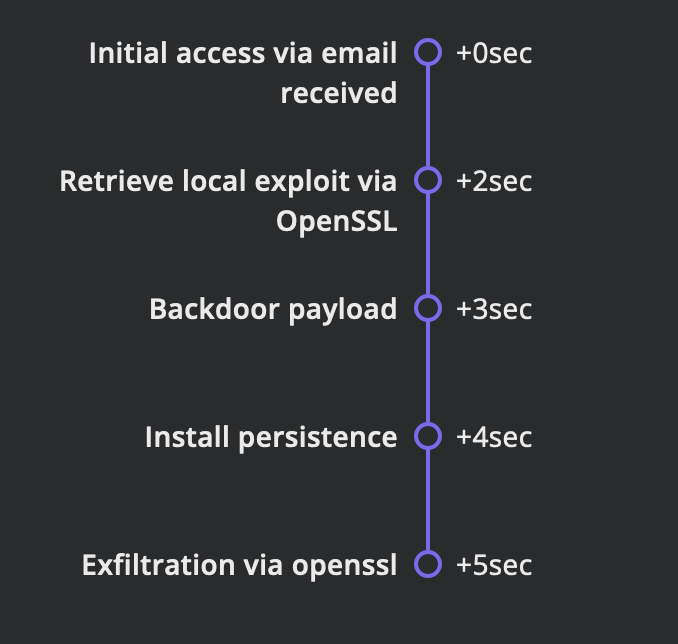
DATA
We are consistently providing data for attacks weekly hoping to contribute raising awareness to threats from their data.
CATEGORY
Dataleak