TLP
TLP CLEAR
Author
David Deflache, Sebastien Tricaud
Summary
In early November 2022, a targeted intrusion began via email, delivering an HTML file utilizing HTML smuggling. Previously relying on Excel macros, the threat actor adapted to Microsoft’s macro control updates. Upon opening the HTML, a disguised Adobe page prompted a ZIP download with a password-protected ISO harboring the malware. The LNK file, posing as a document, triggered rundll32 and a malicious DLL execution. IcedID connected to its command server, maintaining persistence through scheduled tasks. Subsequent phases involved Cobalt Strike, lateral movement, Active Directory reconnaissance, and SessionGopher tool usage. The orchestrated attack culminated in deploying Nokoyawa ransomware, achieving a Time to Ransomware (TTR) of just over 12 hours
TIMELINE
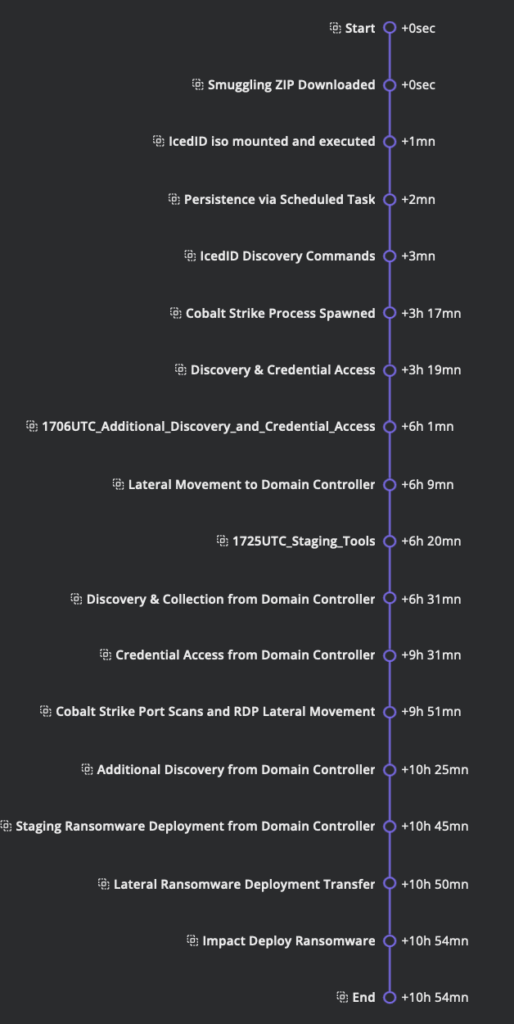
DATA
We are providing data for attacks weekly hoping to contribute raising awareness to threats from their data.
CATEGORY
ransomware