TLP
TLP CLEAR
Authors
Jordi M. Lobo
Summary
BlackByte 2.0 Ransomware Abuses Vulnerable Windows Driver to Disable Security Solutions, believed to be an offshoot of the now-discontinued Conti group, is part of the big game cybercrime crews, which zeroes in on large, high-profile targets as part of its ransomware-as-a-service (RaaS) scheme.
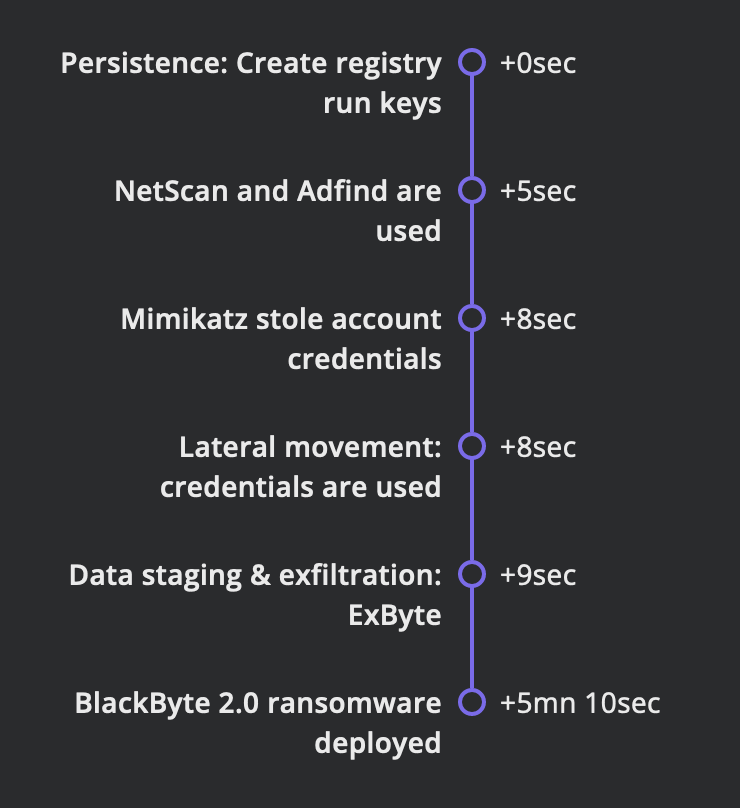
The forensic analysis revealed that the threat actor gained initial access through exploiting ProxyShell vulnerabilities on unpatched Microsoft Exchange Servers. They achieved system-level privileges and created web shells for remote control. A backdoor was installed to collect system information and communicate with a command-and-control (C2) channel. Cobalt Strike Beacon was utilized for persistence, and AnyDesk was used for remote access. Reconnaissance involved network enumeration and Active Directory reconnaissance. Credential theft using Mimikatz was observed. Lateral movement occurred through RDP and PowerShell remoting. Data staging and exfiltration involved a custom tool called ExByte. Data encryption and destruction were carried out using BlackByte ransomware. Recommendations include patch management, endpoint detection and response, and implementing security measures to prevent unauthorized system changes.
DATA
TIMELINE
CATEGORY
Ransomware