TLP
TLP CLEAR
Author
Jordi Lobo
Summary
The exploitation of a critical zero-day vulnerability (CVE-2023-34362) in Progress Software’s MOVEit Transfer solution has been observed. This vulnerability enables remote attackers to gain unauthorized access to the database. Various organizations, particularly in North America, have been affected by this exploitation. The attacker’s behavior appears to be opportunistic rather than targeted. Progress Software has released patches to address the vulnerability and a second SQL injection flaw. Users of MOVEit Transfer are strongly advised to apply the patches immediately and follow emergency incident response procedures. Mitigation guidance, including patch details and indicators of compromise, is provided. The identification of data exfiltration can be achieved through MOVEit event logs. Resources for assessing exposure and detecting exploitation are available.
DATA
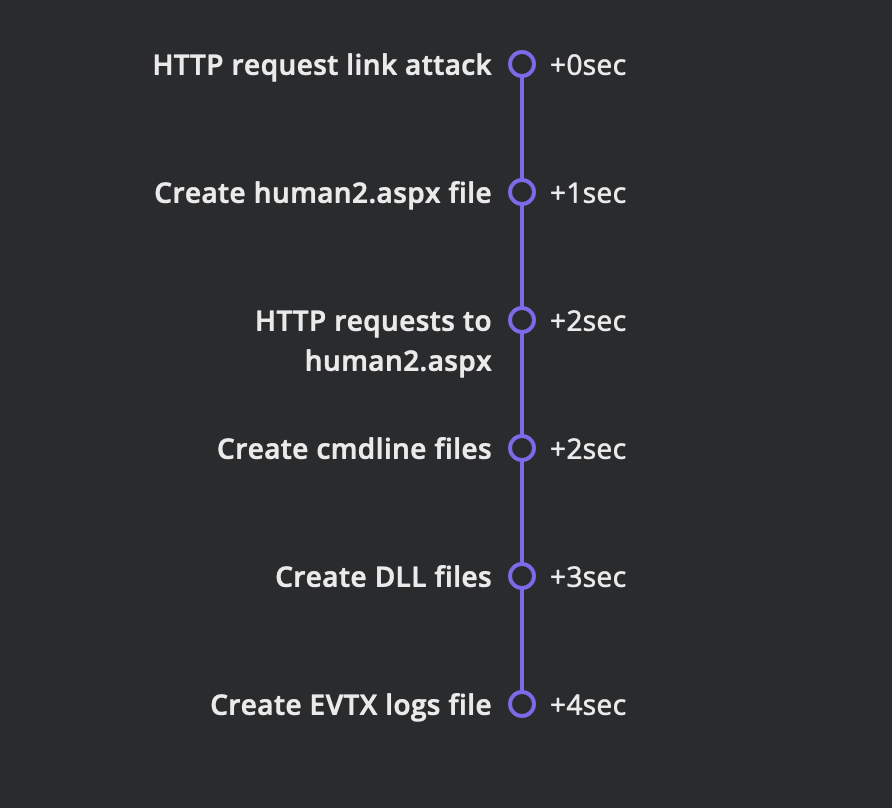
TIMELINE
CATEGORY
Exfiltration
references
- https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-31May2023
- https://www.huntress.com/blog/moveit-transfer-critical-vulnerability-rapid-response
- https://www.mandiant.com/resources/blog/zero-day-moveit-data-theft
- https://www.rapid7.com/blog/post/2023/06/01/rapid7-observed-exploitation-of-critical-moveit-transfer-vulnerability/
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-34362
- https://gist.github.com/JohnHammond/44ce8556f798b7f6a7574148b679c643