TLP
TLP CLEAR
Author
Jordi M. Lobo
Summary
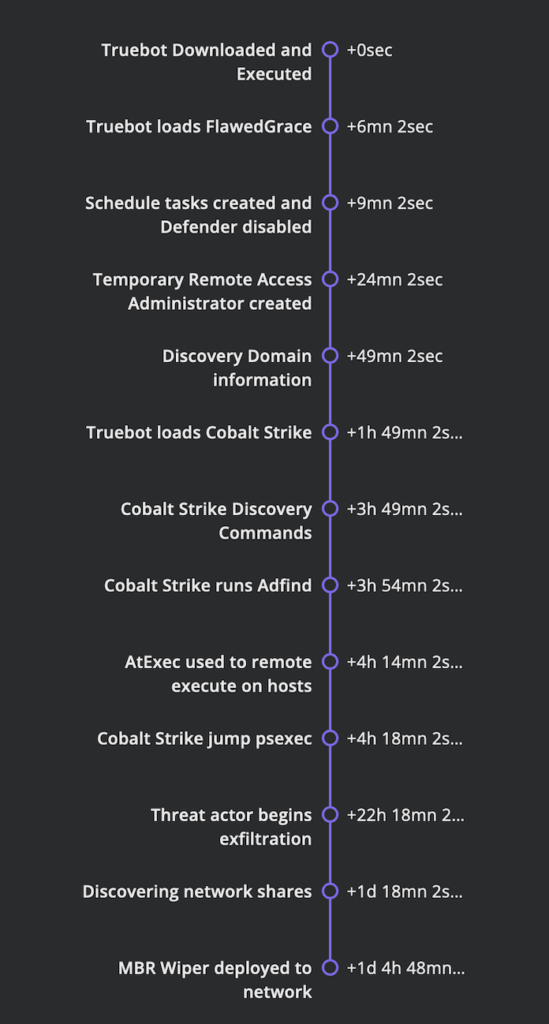
In May 2023, a campaign using the “404 TDS” Traffic Distribution System delivered Truebot via email. Recipients clicking the email link were redirected through multiple URLs, ending in a fake Adobe Acrobat document download that was a Truebot executable. After execution, Truebot copied and renamed, then introduced FlawedGrace malware, using registry and Print Spooler service manipulations for privilege escalation and persistence. FlawedGrace stored/extracted encoded payloads, created tasks, and injected its payload into system processes. Attempts to establish RDP connections and domain exploration followed. Later, Cobalt Strike was introduced, enabling lateral movement and reconnaissance. Data exfiltration and a destructive MBR Killer action ensued, cutting network access.
DATA
TIMELINE
CATEGORY
Malware