TLP
TLP CLEAR
Author
David Deflache, Sebastien Tricaud
Summary
In 2022, a targeted cyberattack employing the WebDav-O malware was identified against a Russian government agency. This malicious activity, linked to the CoughingDown group, spanned back to 2018 and targeted government entities in Belarus. The campaign involved the discovery of multiple WebDav-O variants, with observed commands executed on compromised hosts. The primary objective of the operation is persistent infiltration and espionage within the targeted infrastructure. The CoughingDown group demonstrates a high level of motivation in its clandestine efforts against government agencies in both Russia and Belarus.
TIMELINE
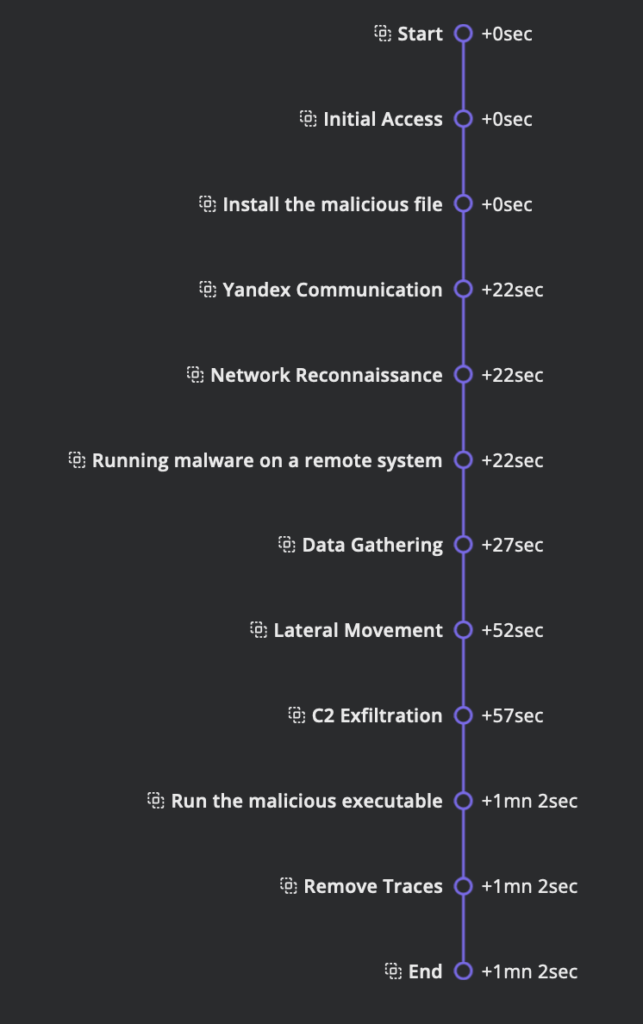
DATA
We are providing data for attacks weekly hoping to contribute raising awareness to threats from their data.
CATEGORY
APT