TLP
TLP CLEAR
Author
David Deflache, Sebastien Tricaud
Summary
This week, we share data from another attack being exploited.
In August 2022, analysts uncovered a cyber attack on a government-run Indonesian company by the APT group GhostEmperor. Known since 2021, GhostEmperor specializes in cyberespionage across sectors, employing tactics such as phishing, software exploits, and network interception. Their targets span government, financial, energy, and technology entities in Southeast Asia, with potential broader impact. While the initial infection vector remains unknown, the attackers, employing Hijack Execution Flow: DLL Side-Loading T1574.002, maintained persistence in the system. GhostEmperor’s primary goals include data theft and espionage, reflecting their persistent and sophisticated threat profile.
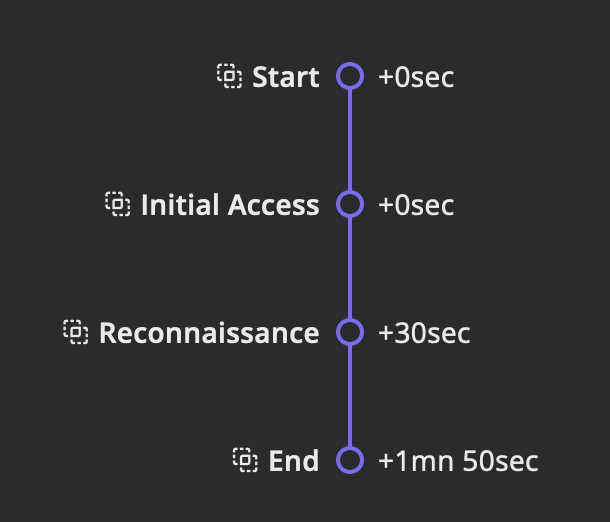
TIMELINE
DATA
We are providing data for attacks weekly hoping to contribute raising awareness to threats as we believe threats are best understood with their data footprint.
CATEGORY
Malware