What Happened?
Last week, Cisco announced a pair of powerful vulnerabilities giving remote command execution capability to adversaries targeting Cisco ASA and FTD products by exploiting Cisco ASA series 5512-X, 5515-X, 5525-X, 5545-X, 5555-X and 5585-X allowing both authentication bypass and complete appliance exploitation, earning a 9.9 CVSS score for one of the most widely deployed firewalls with 17.15% market share on the market today. Cisco has classified these vulnerabilities in CVE-2025-20333 and CVE-2025-20363. CISA has released an Alert for all federal agencies to update their Cisco firewall devices.
Ironically, the detection ecosystem has been relatively quiet. Cisco produced a patch, and folks began the patch process, but the detection engineering capabilities are behind the curve. CISA added these two vulnerabilities to the CISA known exploited vulnerabilities list (KEV), however, few organizations have published detections as a result. A few vendors such as Splunk and Sigma have released some detections to identify exploitation behavior, but we’re going to walk through the entire attack behavior and illustrate why context matters, behavior-defined detections provide more accuracy, and clearly since we are talking about it, agility to deploy detections for critical CVEs as soon as possible may be the difference in outage versus resiliency for many organizations.
How does it work?
Once the vulnerabilities have been successfully exploited, the attacker compromises the device bootloader using RayInitiator for persistence. Once this is done, the “Line Viper” tool is deployed. The following diagram highlights the various steps in the order they happened, along with Indicators of Compromise in Adel.
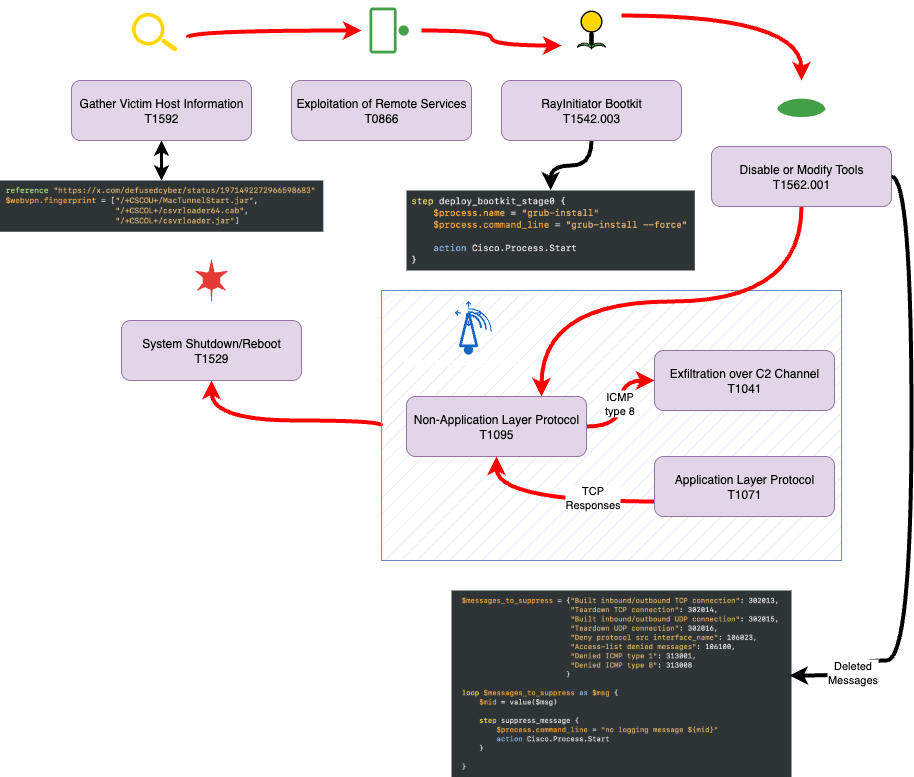
What Detections are Available?
- Splunk: Detection: Cisco ASA – Core Syslog Message Volume Drop
- Proofpoint Emerging Threats: No rules provided in either open or open-nogpl so far.
- Sigma has a pull request for it: Cisco ASA/FP Web Service Exploit
Sigma
title: Cisco ASA/FP Web Service Exploit (CVE-2025-20333 / CVE-2025-20362)
id: 78d976a6-e88c-4876-8211-be89184ce3f3
status: experimental
description: Detects suspicious requests to Cisco ASA/FP web service URLs used for version fingerprinting and exploitation, associated with CVE-2025-20333 and CVE-2025-20362 vulnerabilities.
author: Swachchhanda Shrawan Poudel (Nextron Systems)
date: 2025-09-27
references:
- https://x.com/defusedcyber/status/1971492272966598683
tags:
- attack.t1190
- cve.2025-20333
- cve.2025-20362
- detection.emerging-threats
logsource:
category: webserver
detection:
selection:
cs-method: GET
cs-uri-stem:
- '/+CSCOU+/MacTunnelStart.jar'
- '/+CSCOL+/csvrloader64.cab'
- '/+CSCOL+/csvrloader.jar'
condition: selection
falsepositives:
- Unknown
level: high| 🤩 The Good | 😟 The Bad | 😱 The Ugly |
| * Detects device fingerprinting before attacking | * It will not detect the attack | * High false positives rate from scripts doing discovery * Not related to the remote exploit * Only one sign that could be the attack precursor but not reliable |
Splunk
`cisco_asa`
| rex "%ASA-[^-]+-\d+-(?<message_id>\d+):"
| search message_id IN (302013,302014,609002,710005)
| eval msg_desc=case(
message_id="302013","Built inbound TCP connection",
message_id="302014","Teardown TCP connection",
message_id="609002","Teardown local-host management",
message_id="710005","TCP request discarded"
)
| bin _time span=15m
| stats count values(msg_desc) as message_description values(host) as host by _time message_id
| xyseries _time message_id count
| `cisco_asa___core_syslog_message_volume_drop_filter`| 🤩 The Good | 😟 The Bad | 😱 The Ugly |
| * It displays one attacker behavior for this specific attack * Check directly against Cisco ASA logs, where the attack occurs | * In a production environment, multiple machines will not be compromised at the same time, the 15 minutes span will not be enough * This is not an alert but a statistics that requires an operator to look at | * The attack runs many other things which are not captured * Missing other observed message ids being dropped: 302015, 302016, 313001, 313008 * Attacker also discards any log below warning (logging trap warnings) |
Detecteam automatically generated detections
- CVE-2025-20333 is using valid logins with specifically crafted HTTPs requests
- CVE-2025-20363 with unauthenticated access
- Bootkit installation
- System unusual shutdown/start
- Traps set for data
- Network traces for ICMP type 8 with data and no response following by a TCP tunnel establishment
Conclusion
Detections are not useful without context, this is why we attach them in constellations: there would be a high level of false positives if those detections were isolated.
They actually make a stronger case towards reliable detection if together.
At Detecteam, this is exactly what we do to help our customers: attacks are stories, not isolated events, this is why they are organized by threat actors, capability, campaigns etc. Why is this only organized this way to describe attacks but never for defense?
Why Detecteam
While public detections of the recent attack appear limited, Detecteam’s REFLEX™ platform specializes in developing, testing, validating and deploying robust detection mechanisms for various integrations, including Splunk, Elastic, Sekoia, and Devo, by leveraging attack behaviors. Because we generate precise data reflecting adversary behaviors, Detecteam’s detections are accurate to the threat behavior. Details matter when discussing speed, coverage, and quality. Accuracy is the validation you are actually prepared for this behavior and have evidence from testing and provenance in the data used to tell the detection story. Close the loop on your detection development lifecycle in minutes not months.
For context-aware and rigorously tested quality detections, we are happy to support your requirements.
References
CISA Alert: CISA Directs Federal Agencies to Identify and Mitigate Potential Compromise of Cisco Devices
Cisco exploited vulnerabilities: CVE-2025-20333, CVE-2025-20362, CVE-2025-20363
Cisco ASA market share: https://6sense.com/tech/perimeter-security-and-firewalls/cisco-asa-market-share
Cisco attack details: Continued Attacks Against Cisco Firewalls
UK National Cyber Security Centre report: Malware Analysis Report: RayInitiator & LINE VIPER
Splunk Detection: Cisco ASA – Core Syslog Message Volume Drop
Sigma Pull Request: Cisco ASA/FP Web Service Exploit
Azure Sentinel unofficial detection: Cisco ASA Zero-Day Duo Under Attack CVE-2025-20333