TLP
TLP CLEAR
Author
David Deflache
Summary
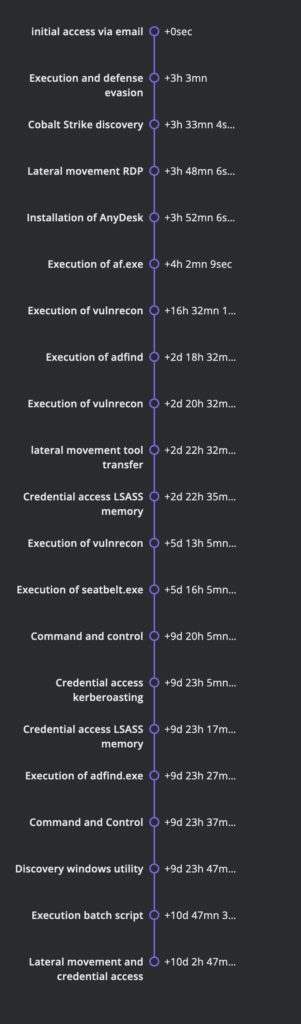
This case involves a sophisticated intrusion that occurred over an 11-day period. The threat actors initiated the attack by sending an email with a link to download a password-protected zip file containing an ISO file. Upon extraction, the ISO file mounted as a CD and executed a hidden DLL file, introducing the Bumblebee malware loader. The loader established communication with the Bumblebee command-and-control servers and dropped a Cobalt Strike beacon on the compromised system. The threat actors then conducted reconnaissance using various Windows utilities and gained RDP access to a server using the local Administrator account. They deployed AnyDesk for persistence and performed Active Directory and privilege escalation discovery. The intrusion culminated with preparations for a domain-wide ransomware deployment, but the threat actors were evicted before executing their final actions.
DATA
TIMELINE
CATEGORY
Malware
references
- https://thedfirreport.com/2022/08/08/bumblebee-roasts-its-way-to-domain-admin/
- https://www.crowdstrike.com/blog/getting-the-bacon-from-cobalt-strike-beacon/