TLP
TLP CLEAR
Author
Jordi M. Lobo
Summary
Mallox is a ransomware strain that targets Microsoft Windows systems and has been active since June 2021. Recently, Unit 42 researchers observed a significant increase in Mallox ransomware activities, with a rise of almost 174% compared to the previous year. The group exploits unsecured MS-SQL servers as a penetration vector to compromise victims’ networks. They employ brute force attacks, data exfiltration, and network scanners to distribute the ransomware. Mallox follows the double extortion trend, stealing data before encrypting files and threatening to publish it on a leak site to pressure victims to pay the ransom.
DATA
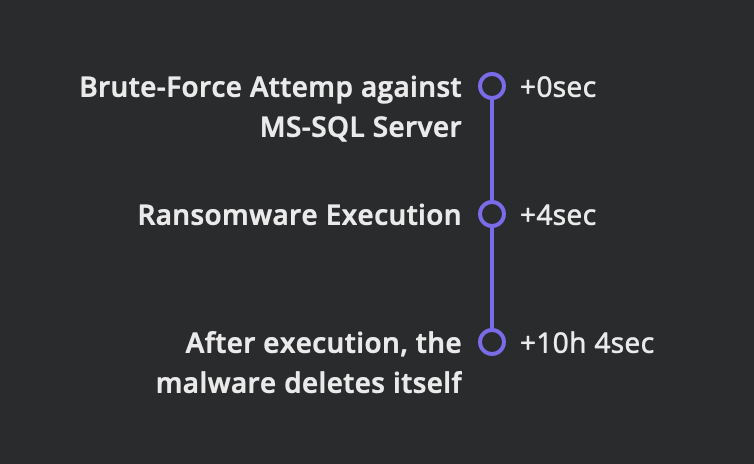
TIMELINE
CATEGORY
Ransomware
references
- https://unit42.paloaltonetworks.com/mallox-ransomware/
- https://www.hivepro.com/wp-content/uploads/2022/12/Mallox-Ransomware-is-Ramping-up-its-Operation_TA2022300.pdf
- https://blog.cyble.com/2022/12/08/mallox-ransomware-showing-signs-of-increased-activity/