TLP
TLP CLEAR
Author
David Deflache, Sebastien Tricaud
Summary
This week, we share data from another attack being exploited.
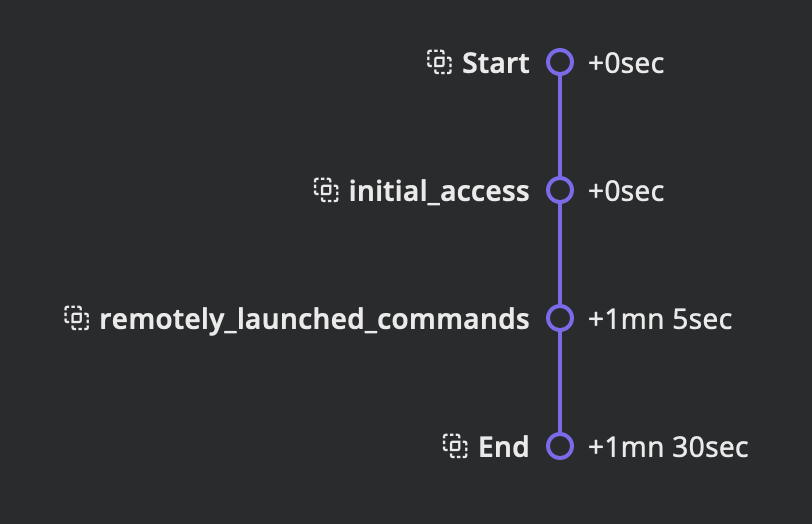
In mid-Autumn 2021, Kaspersky experts uncovered a ShadowPad malware campaign targeting a national telecom company in Pakistan. The attack, presumed to have begun in winter 2021, exploited MS Exchange vulnerability (CVE-2021-26855) to install a Cobalt Strike backdoor. ICS engineers’ computers and automation systems were compromised, with a persistent presence for at least 11 months. The attackers utilized a Web Shell in the victim’s mail server, employing DLL Side-Loading (T1574.002) characteristic of Asian APT groups. ShadowPad samples were also found in Afghanistan and a Malaysian transportation company, suggesting a broad geographic scope. The likely motive is cyberespionage for critical data.
TIMELINE
CATEGORY
Malware