TLP
TLP CLEAR
Author
Jordi M. Lobo
Summary
The Vice Society ransomware group gained notoriety in late 2022 and early 2023 for launching attacks across various sectors, including San Francisco’s transit system. While education and healthcare were their primary targets, Trend Micro’s data reveals manufacturing industry infiltration in Brazil, Argentina, Switzerland, and Israel. Exploiting the PrintNightmare flaw initially, Vice Society progressed to self-made ransomware and potent encryption, possibly signaling their move towards a ransomware-as-a-service venture. With previous ransomware versions like Hello Kitty/Five Hands and Zeppelin, their evolving tactics showcase a versatile threat actor aiming to breach diverse industries using compromised credentials from underground sources.
DATA
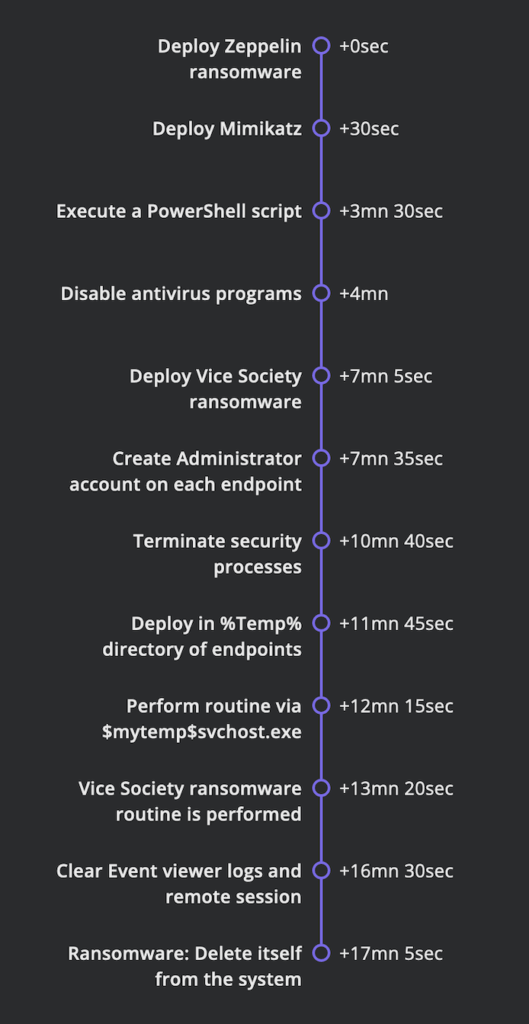
TIMELINE
CATEGORY
Ransomware