-
Simulating and Detecting React2Shell: A Deep Dive into CVE-2025-55182 & CVE-2025-66478
Introduction When critical vulnerabilities emerge in widely-deployed frameworks, security teams face an immediate challenge: how…
-
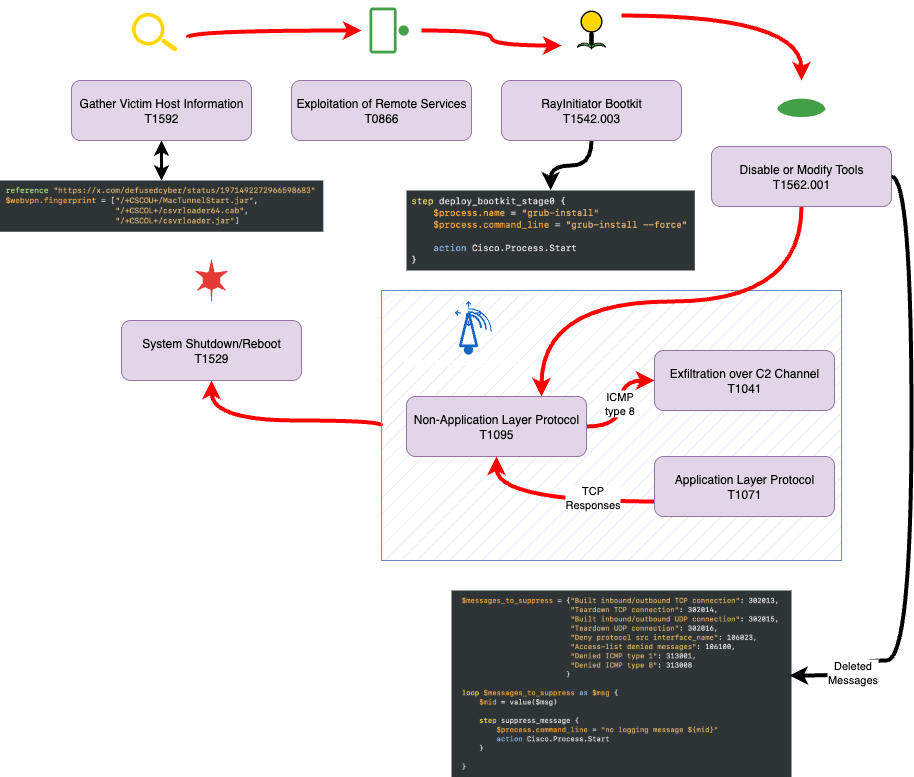
Detecting the Cisco ASA RCE Exploitation 5500-X series attack?
What Happened? Last week, Cisco announced a pair of powerful vulnerabilities giving remote command execution…
-
Detecting Salesforce leaks after Salesloft Drift breach
Summary Salesloft was breached in August, resulting in Drift marketing token re-use in Salesforce based…
-
Scattered Spider: Detection Engineering Dilemma
Scattered Spider is a rapidly emerging threat. As a native English-speaking group, it has quickly…
-
Detecteam: The Crossroads of Security and Reality
Meet Detecteam, your new favorite over-achiever in security detection. We’ve built an innovative pipeline for…